Hi Bo,
Please help to add the following SPs for SFD Motion to the agenda:
SP1
- Do you agree to add the following text to TGbp SFD?
- Control information that may be sent from the AMP AP to the AMP Energizer relating to the excitation signal includes one or more of the following: Start Time,
Duration, Transmit Power and frequency related parameters.
- The frequency related parameters may include central frequency information, etc.
SP2
- Do you agree to add the following text to TGbp SFD?
-
IEEE 802.11bp allows a non-AP AMP STA to report the transmission time it can sustain. How the non-AP AMP STA determines the time is TBD.
-
Note:
-
The AP may derive the reception or idle time based on this transmission time.
-
The idle time refers to the time in a mode of operation with no RF activity, i.e. the non-AP AMP STA cannot transmit or receive any frames in this mode.
-
The AP may derive the reception or idle time based on this transmission time.
SP3
- Do you agree to add the following text to TGbp SFD?
- IEEE 802.11bp defines an AMP Open Service Period, that allows an Active Tx non-AP AMP STA to enter doze state after a minimum wake up time since the start of
the AMP Open Service Period, if the Active Tx non-AP AMP STA does not receive any AMP DL PPDU from the AMP AP.
- Do you agree to add the following text to TGbp SFD?
Thanks and Regards
Ian
From: lipanpan (D) <00002fa7231ab79a-dmarc-request@xxxxxxxxxxxxxxxxx>
Sent: Thursday, 15 May 2025 8:23 am
To: STDS-802-11-TGBP@xxxxxxxxxxxxxxxxx
Subject: Re: [STDS-802-11-TGBP] [EXT] Re: [STDS-802-11-TGBP] SP request
Hi Bo,
Could you please help queue the following SP for the May meeting agenda?
- Do you agree to add the following text to TG bp SFD?
- 11bp defines at least one mode of MAC/PHY that supports mono-static backscattering communication in sub-1 GHz.
- 11bp defines at least one mode of MAC/PHY that supports mono-static backscattering communication in sub-1 GHz.
Supporting contribution: [11/25-0816]
Thank you!
Panpan
From: Nelson Costa <nelson@xxxxxxxx>
Sent: Thursday, May 15, 2025 10:59 AM
To: STDS-802-11-TGBP@xxxxxxxxxxxxxxxxx
Subject: Re: [STDS-802-11-TGBP] [EXT] Re: [STDS-802-11-TGBP] SP request
Hi Bo,
Could you please help queue the following SPs for the May meeting agenda?
[SP1]
Do you agree to add the following content to TGbp SFD?
. 11bp defines one mode of backscattering with carrier center frequency shift.
Supporting contributions: 11-25/0265, 11-25/0265
[SP2] (informational only)
Do you agree that 11bp should define at least one standard receiver model?
Supporting contribution: 11-25/0806
Thank you!
Nelson.
On Wed, May 14, 2025 at 5:17 PM Rui Cao <rui.cao_2@xxxxxxx> wrote:
Hi Bo,
Please add the following SP to the agenda:
SP1: Do you agree to add the following to 11bp SFD?
- The SYNC, Data field and Excitation field of 11bp DL PPDU use OFDM symbol as base carrier waveform for OOK modulated AMP communication.
Supporting contribution: [11-25/0797, 11-25/0305, 11-25/0325]
SP2: Do you agree to add the following to 11bp SFD?
- The base OFDM symbol is defined as 4us OFDM symbol, and generated by performing 64-point IFFT of the predefined sequence and pre-append the last 0.8us waveform as the cyclic prefix
Supporting contribution: [11-25/0797, 11-25/0305, 11-25/0325]
SP3: Do you agree to add the following 11bp SFD?
- The maximum allowed clock inaccuracy for the backscattering tag using OOK modulation is 100,000 ppm for both receive mode and backscattering transmit mode?
Supporting contribution: [11-25/0798, 11-24/1237]
Thanks,
Rui
From: You-Wei Chen <ywchen77115@xxxxxxxxx>
Sent: Wednesday, May 14, 2025 1:33 PM
To: STDS-802-11-TGBP@xxxxxxxxxxxxxxxxx
Subject: [EXT] Re: [STDS-802-11-TGBP] SP request
Caution: This is an external email. Please take care when clicking links or opening attachments. When in doubt, report the message using the 'Report this email' button
Dear Bo,
Can you add the following SP to the SP list? many thanks
- Do you agree to add the following text to TGbp SFD?
- IEEE 802.11bp defines 4 base sequences used for AMP DL/UL SYNC field in 2.4GHz frequency band.
- 1 base sequences, S1, for DL non-backscatter SYNC field. S1 and a function of S1, are used for different DL data rate.
- 1 sequence, S2, for DL backscatter SYNC field.
- 1 base sequence, S3, for UL active transmission SYNC field.
- 1 sequence, S4, for UL backscatter SYNC field.
- Detailed SYNC sequence designs are TBD
- Besides the above 4 base sequences, the need of additional sequence S5 is TBD if mono-static and bi-static backscattering UL SYNC field design is different.
BR,
You-Wei Chen
Sanket Kalamkar <000033b8f79f2eb4-dmarc-request@xxxxxxxxxxxxxxxxx> 於 2025年5月14日 週三 下午2:40寫道:
Hi Bo,
Can you please help queue the following SPs for 11bp May meeting agenda? All SPs are for SFD motion.
[SP1] Do you agree that 802.11bp defines an AMP Wake-Up frame, which an AMP AP transmits to AMP-enabled non-AP STA(s) to indicate that the AP intends to exchange non-AMP frames with the non-AP STA?
o The expectation is to reuse WUR frame format for the AMP Wake-Up frame and to carry it in an AMP PPDU
Supporting contribution: 11-25/0779r0
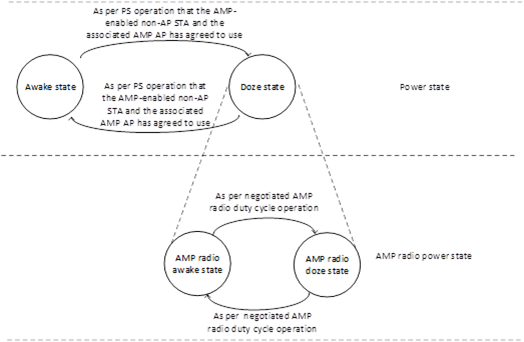
[SP2] Do you agree that 802.11bp defines an AMP duty cycle operation for an AMP-enabled non-AP STA, which follows the state transition diagram shown in the figure?
o AMP duty cycle operation follows the negotiation procedure defined for WUR in the baseline
Supporting contribution: 11-25/0779r0
[SP3] Do you agree that if an AMP-enabled non-AP STA successfully receives an AMP Wake-Up frame from the associated AMP AP, the non-AP STA should transition to the Awake State and transmit a PS-Poll/UL frame to the AP to indicate that it is in the Awake State (PS/Active mode)?
Supporting contribution: 11-25/0779r0
[SP4] Do you agree that if the non-AP STA transmits a frame with PM = 1 to the associated AP, then the non-AP may transition to the Doze state, and the AMP-enabled non-AP STA shall enter the AMP mode?
Supporting contribution: 11-25/0779r0
[SP5] Do you agree that 802.11bp defines:
o AMP temporal key (ATK) to protect individually addressed AMP frames
o AMP integrity group temporal key (AIGTK) to protect group addressed AMP frames
Supporting contribution: 11-25/0779r0
[SP6] Do you agree that 802.11bp uses the baseline authentication procedure to generate AMP temporal key(s) to protect individually and group addressed AMP frames?
Supporting contribution: 11-25/0779r0
[SP7] Do you agree that an AMP-enabled non-AP STA and the associated AMP AP use AMP mode setup to exchange AMP capabilities?
o AMP mode setup may occur during the association procedure or post-association
Supporting contribution: 11-25/0779r0
[SP8] Do you agree that the clock error requirement of an AMP-enabled non-AP STA in AMP power state is the same as that of an Active Tx non-AP AMP STA?
Supporting contribution: 11-25/0779r0
[SP9]: Do you agree that 802.11bp defines a mechanism to generate a transient key at the AMP client to support secure communication, where:
- An AP transmits a downlink frame containing an ANonce.
- After receiving the downlink AMP frame from the AP that contains an ANonce, an AMP client generates an SNonce.
- The client generates a transient key using the ANonce, the SNonce, and a Pairwise Master Key (PMK) between the AP and the client.
- Note1—The mechanism to generate PMK is TBD.
- Note2—Whether to include backscatter clients is TBD.
Supporting document: 11-24/2112
[SP10]: Do you agree that 802.11bp defines a mechanism to generate a transient key at the AP to support secure communication, where:
- In response to the downlink AMP frame from the AP that contains an ANonce, the AMP client transmits an uplink AMP frame that carries the SNonce and a MIC.
- The client generates the MIC using the derived transient key at the client.
- If the MIC is verified, the AP uses the ANonce it transmitted in the previous downlink AMP frame, the SNonce, and the PMK to generate the transient key.
- Note—Whether to include backscatter clients is TBD.
Supporting document: 11-24/2112
[SP11]: Do you agree that the transient key generation at the AP and the AMP client in 802.11bp may occur concurrently with AMP downlink and uplink data communication:
· The downlink AMP frame from the AP carries ANonce along with downlink data from the AP (e.g., AMP trigger).
· The uplink AMP frame from the AMP client carries SNonce and MIC along with the UL data (e.g., UL response to the AMP trigger).
· Note—Whether to include backscatter clients is TBD.
Supporting document: 11-24/2112
[SP12]: Do you agree that the transient key generation at the AP and the AMP client in 802.11bp may be performed immediately before AMP downlink and uplink data communication:
- Once the transient key is derived at both the AP and the AMP client, subsequent AMP data communication between the AP and the client can be secured using MIC and/or encryption based on the generated transient key.
- Note—Whether to include backscatter clients is TBD.
Supporting document: 11-24/2112
Best,
Sanket
To unsubscribe from the STDS-802-11-TGBP list, click the following link: https://listserv.ieee.org/cgi-bin/wa?SUBED1=STDS-802-11-TGBP&A=1
To unsubscribe from the STDS-802-11-TGBP list, click the following link: https://listserv.ieee.org/cgi-bin/wa?SUBED1=STDS-802-11-TGBP&A=1
To unsubscribe from the STDS-802-11-TGBP list, click the following link: https://listserv.ieee.org/cgi-bin/wa?SUBED1=STDS-802-11-TGBP&A=1
To unsubscribe from the STDS-802-11-TGBP list, click the following link:
https://listserv.ieee.org/cgi-bin/wa?SUBED1=STDS-802-11-TGBP&A=1
To unsubscribe from the STDS-802-11-TGBP list, click the following link:
https://listserv.ieee.org/cgi-bin/wa?SUBED1=STDS-802-11-TGBP&A=1
To unsubscribe from the STDS-802-11-TGBP list, click the following link: https://listserv.ieee.org/cgi-bin/wa?SUBED1=STDS-802-11-TGBP&A=1